As cars and commercial vehicles become increasingly connected, cybersecurity risks increase as well. As a result, from July 2024, new vehicles will only be registered in the EU if their manufacturers can guarantee secure operation with appropriate solutions to ward off attacks and to detect and eradicate vulnerabilities.
The importance of cybersecurity in vehicle, tool and software development can be seen in one of the most famous vehicle hacks from 2014: the complete takeover of a Jeep Cherokee by security researchers Charlie Miller and Chris Valasek. They had initially used WLAN to gain access to the onboard network and were ultimately able to use mobile communications to take complete control of all components connected to the CAN bus. Steering wheel, engine, transmission and the braking system, and in addition they could also remotely control windshield wipers, air conditioning and door locks, for example.
As a consequence, Chrysler had to recall around 1.4 million vehicles to workshops for a security update. The U.S. mobile communications provider Sprint, which was responsible for networking the Jeeps, also had to eliminate weaknesses in its network. A 2015 survey by market analysts Kelley Blue Book found that 72 percent of the drivers surveyed had heard of the hack; 41 percent said it would influence their decision the next time they bought a car.
Although this case was a wake-up call for the automotive industry, new security problems have continued to cause millions of recalls since then. Further evidence of the high risk of compromise was provided by NDIAS security researchers at the DEF CON 28 security conference in 2020, where they presented an examination of 40 ECUs sourced from ten different premium manufacturers. In their research, they had found more than 300 security vulnerabilities that could have been exploited by hackers. 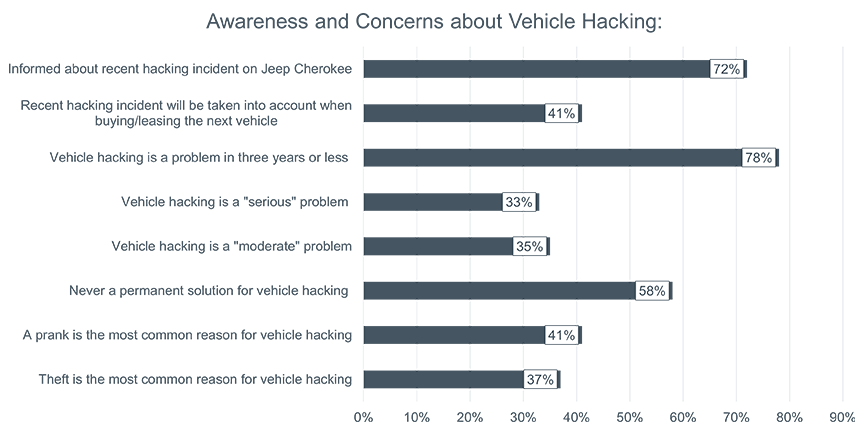
è Full results of the survey with specific numbers and responses at https://mediaroom.kbb.com/nearly-80-percent-consumers-think-vehicle-hacking-important-frequent-problem-future, section „Awareness and Concerns about Vehicle Hacking“
Networking progresses
In addition to attacks on software and systems directly at the manufacturer, increasing networking provides the largest attack surface. The consulting firm Accenture expects one billion vehicles worldwide to be connected by 2040. The demand from buyers is also driving this trend, opening up new sales opportunities for vehicle manufacturers. The latest survey on digital functions in vehicles conducted by Civey on behalf of eco, the German Internet Industry Association, shows that German car buyers are open to a wide range of offers (see Fig. 1). Most of these, however, require data communication to outside systems - potentially creating additional risks. 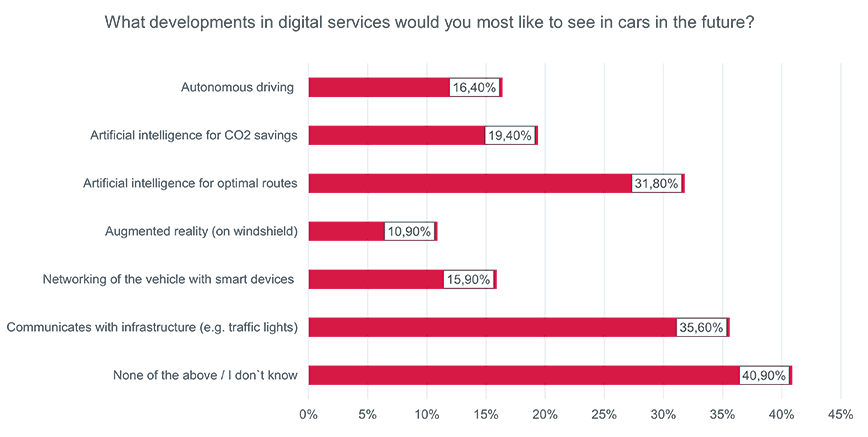
The market research company Upstream additionally cites the greater use of software - up to and including the software-defined vehicle (SDV) - as another cause for rising security risks. Furthermore, backend servers would also be attacked, as would the charging infrastructure of electric vehicles and all applications that establish a connection between them or the vehicles - those can also come from third-party manufacturers. According to an analysis of nearly 1,300 automotive cybersecurity incidents between 2010 and the first half of 2023, 30 percent of incidents had a potential impact on data privacy. This includes access to customer data and the intellectual property of manufacturers, along with threats to vehicle safety and theft protection. In the current year, data breaches increased and accounted for 37 percent of the recorded incidents.
Thus, much more effort needs to be made to ensure vehicle cybersecurity. Market researchers at Precedence Research expect vehicle manufacturers' expenses in this segment to grow by more than 18 percent annually, increasing more than fivefold from 2022 to 2032. They forecast global automotive industry expenses of nearly $16.5 billion worldwide by 2032. 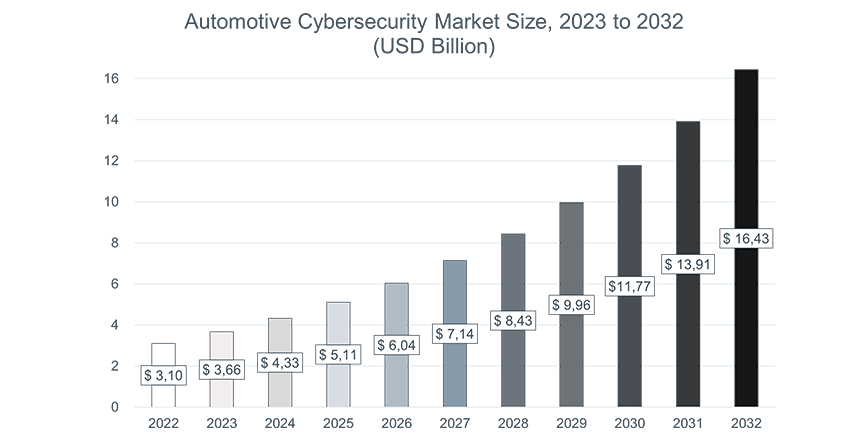
Stricter regulation by UNECE R155 & Co.
For this reason, the United Nations Economic Commission for Europe, UNECE, adopted new regulations in 2021 to help ensure effective protection of vehicles by manufacturers. The UNECE R155 regulation requires OEMs to install an effective Cybersecurity Management System (CSMS) for risk detection and mitigation in all new vehicle classes since July 2022. These include Threat Analysis and regular Risk Assessment (TARA) and monitoring of new vulnerabilities and known attacks to be able to react with new updates. Starting in July 2024 - less than a year from now - this will be mandatory for all new vehicles in the EU.
Manufacturers are therefore ultimately responsible for continuous security improvements and risk prevention throughout the entire life cycle of the vehicle. They have to target the risks along the supply chain and regularly reassess the risk situation, and react to changing threat situations due to emerging vulnerabilities. This is a major challenge, for example when you look at the software being used, most of which comes from third-party suppliers.
Related to UNECE R155 is the ISO/SAE 21434 standard, titled "Road Vehicles - Cyber Security Engineering." As the name suggests, it defines procedural and organizational requirements to ensure robust cybersecurity for vehicles throughout their lifecycle, from conception through production and operation to decommissioning. Manufacturers and suppliers alike must demonstrate compliance with this quality standard through certification.
In connected vehicles, software updates and security patches are often applied remotely via mobile communications. In principle, these over-the-air updates (OTA updates) in turn pose a security risk. This is also regulated through UNECE R156, which requires a secure Software Updates Management System (SUMS). The implementation must also be proven to the supervisory authorities and certification will be carried out in accordance with the ISO 24089 standard adopted in the past.
Compliance support
Compliance with UNECE R155 and R156 with implementation and operation of the required CSMS and SUMS solutions are part of the requirements of the type approval procedure of the German Federal Motor Transport Authority (KBA). The KBA has set out how these can be demonstrated in its comprehensive "Catalog of requirements for auditing cybersecurity/SU management systems".
EDAG's CSMS framework provides a solution that solves many of the challenges of UNECE R155 and ISO/SAE 21434, providing essential support for regulatory compliance. The framework includes the components Tool Management, Cybersecurity Monitoring, Vulnerability Analysis and Vulnerability Management.
The system is also user-friendly in application. Customers can easily integrate the analysis tool into their build pipelines. A scanning process within software projects creates a data set that includes an SBOM (list of tools and technologies used) and NBOM (list of sources of tools and technologies used) of the current version.
The Vulnerability Monitoring component scans multiple public sources for common vulnerabilities and exposures and stores the information in the reporting dashboard. It also compares them with technologies used in current or previous customer projects. Users and customer teams can be automatically notified if CVEs (Vulnerabilities reported to Common Vulnerabilities and Exposures) surface for any of their projects. Alternatively, scans of current and past projects can be started manually if required.
In addition, a Git Commit Hash is stored in a log for each compiling procedure. This enables the user to track all the technologies (tools, frameworks, packages and libraries) used in their projects and reproduce exactly the same build environment that was used to compile those projects.
Efficient safety gain
Thus, with the help of the EDAG CSMS Framework, users can always track which technologies were used in which projects, where they originated, and which vulnerabilities are publicly known for these technologies. The reports can be accessed via the integrated dashboard or exported as PDF, CSV and the industry standard CycloneDX (JSON) format. Particularly interesting for suppliers: They can send these to OEMs together with the binaries without having to release their source code. 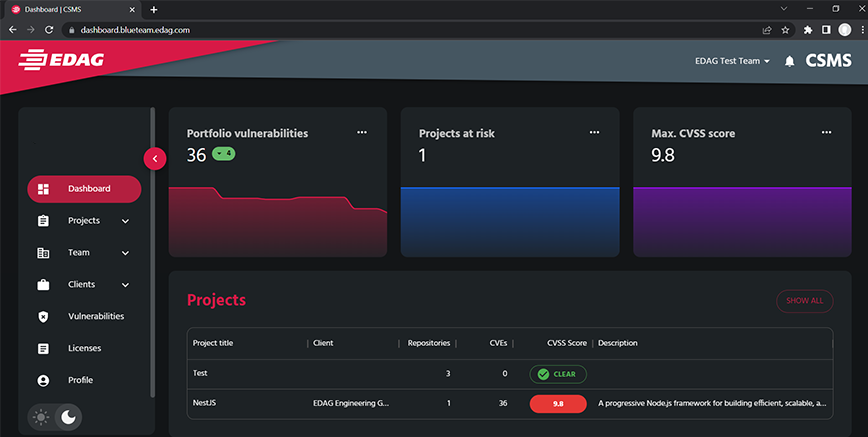
Thanks to its easy integration and complete coverage of the required security functions, the EDAG CSMS Framework helps to reduce the manual engineering effort and at the same time sustainably improve the security level.
If you want to learn more about how to efficiently meet regulatory requirements and see EDAG's CSMS, you can register right here for our webinar recording "How to ensure more security in mobility through a cybersecurity management system". Laurin Schnell, Project Manager Software Development at EDAG Engineering, will be happy to answer any further questions you may have about improving cybersecurity around the vehicle and vehicle development.





