In order to integrate medical devices into a medical ecosystem, they must be able to communicate. To this end, manufacturers are upgrading their devices with connectivity features. Functions such as over-the-air updates, remote measurements, and remote alarms are at the forefront of retrofitting. Those who push ahead with modernization without careful planning risk disadvantages due to the need for recertification. But that doesn't have to be the case. Here is an overview of how you can strategically plan and implement innovations to keep costs and time-to-market low.
If medical devices only output their data in analog form, such as ECG curves on paper strips, or if examination results can only be downloaded manually, then this is no longer in line with the times. Digitalization in healthcare is advancing inexorably. Cost pressures and staff shortages are forcing clinics, nursing homes, and medical practices to streamline their processes by eliminating unnecessary manual tasks and speeding up workflows. The biggest levers in this direction are automation and device networking.
Unimpeded but secure data transmission, remote operation, and automatic alerts when vital signs exceed limits or other dangerous conditions are detected during monitoring are therefore among the most important functions of a modern medical infrastructure. MedTech providers are under pressure to adapt their products to these requirements and retrofit interfaces for data transmission where these are currently lacking.
Regulatory requirements and hurdles
From a technical point of view, the integration of bidirectional communication interfaces can be considered a manageable task. The real challenges lie more in the area of regulatory requirements. In view of the increasing software content of modern medical devices, the EU Medical Device Regulation (MDR 2017/745), for example, requires a post-market surveillance system that continuously addresses responsibility for software errors and security vulnerabilities.
The mechanisms for distributing updates and patches are themselves considered a safety-relevant component of device development. Standards such as ISO 13485 (quality management), ISO 14971 (risk management), and IEC 62304 (software life cycle) require device manufacturers to distribute software changes and security updates in a systematic, traceable, and secure manner.
When integrating the OTA update function, manufacturers must be aware that the existing conformity assessment (CE) may lose its validity and require a reassessment if it is considered a "significant change." Reassessment by a notified body means an additional time expenditure of 6 to 18 months, associated with considerable costs. Those who want to make a conscious leap in innovation with retrofitted networking cannot avoid the consequences of necessary recertification. However, those who only want to adapt to the new requirements of a modern medical infrastructure must thoroughly prepare their decision on development goals and scope in order to avoid unnecessary certification costs.
The "right" dose of innovation
Based on an impact analysis carried out in-house, various alternatives can be reviewed to determine whether they necessitate recertification. To do this, three key questions must be answered with regard to the planned changes:
- Does the intended purpose change?
- Is the risk or software class changing?
- Does a new clinical risk arise?
The answers provide information about the effort required for (re)entry into the market. Only if one of these questions is answered with "yes" is recertification likely.
Here are a few typical examples at a glance: 
Device manufacturers who want to be on the safe side and avoid recertification should therefore observe a few principles during modernization that must be followed by the development team:
- Maintain intended purpose: The OTA update must not introduce any function that changes the medical intended purpose.
- Maintain risk profile: Every change must be assessed for its risk impact in accordance with ISO 14971.
- Software testing according to IEC 62304: Regression testing is mandatory to avoid unintended side effects.
- Ensure cybersecurity: Updates must be signed, encrypted, and traceable.
- Transparent documentation: Changes must be integrated into the quality management system (QMS) – even if recertification is not necessary.

Here is an excerpt from our Quick Check form, which you can use to create a simple impact analysis and derive the necessary steps. The complete document is part of the supplementary white paper.
Use case: OTA updates for an ECG device
How this works in practice can be illustrated using the example of an ECG device that does not yet have modern connectivity. The aim is to make it fit for automated updates via a wireless communication interface (over-the-air updates, OTA). In doing so, a whole range of regulatory requirements relating to data and communication security must be observed. These extend far beyond the device itself:
- Update server (cloud): The integrity and authenticity of each update must be verified by a secure signature. Strict change and release management as well as documentation for technical documentation (MDR) are mandatory, as updates directly affect the safety and usability of the device.
- OTA channel (from the cloud to the device): The transmission must be end-to-end encrypted and authenticated. It must be proven that transmission errors (due to network failover, retry mechanisms, and transaction logs) cannot cause harm to patients. In addition, high cybersecurity requirements apply.
- Gateway/edge: If a gateway performs update distribution or validation tasks, it itself becomes a medical device or accessory and is therefore subject to regulation, including responsibility for risk minimization and version management.
- Device: The device must have a secure bootloader, redundant storage partitions (A/B) for fail-safe mechanisms, and secure device identity management. The software life cycle must be fully documented in accordance with IEC 62304. In addition, it must be demonstrated that updates do not trigger a critical condition and that electrical safety (e.g., according to IEC 60601) is always maintained.
- Feedback/telemetry (cloud): For post-market surveillance (PMS), there is an obligation to document errors, rollbacks, and safety incidents and, if necessary, report them in PMS reports or vigilance reports (MDR).
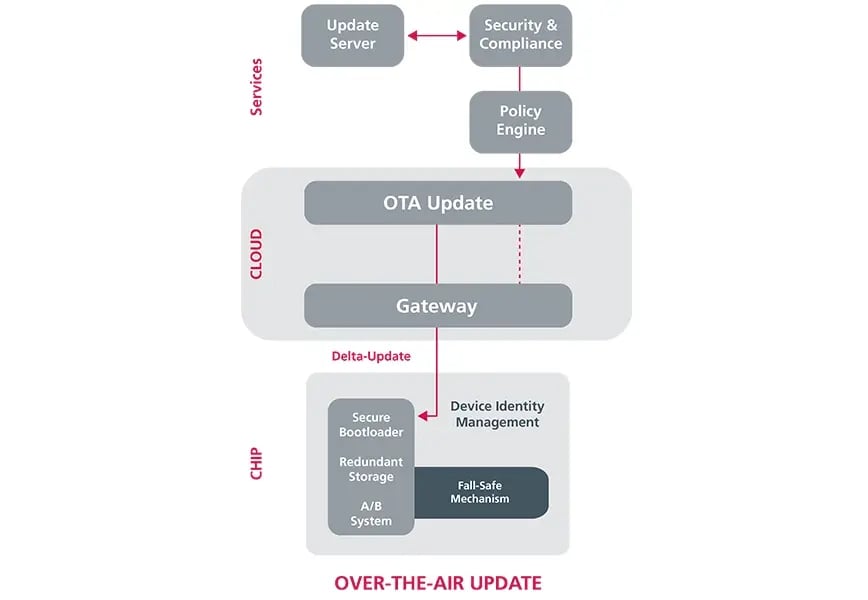
The most important elements for a secure, reliable OTA update process.
This leads to a series of development goals and requirements that must be worked through in order to implement OTA retrofitting on the technical side. It is clear that data communication, over-the-air updates, data protection, and cybersecurity are all software-driven issues. In some cases, device manufacturers simply lack the capacity, but in others they also lack the expertise to drive the innovations required for over-the-air updates. They are therefore relying on collaboration with external development service providers to fill the existing gaps.
Finding external support
However, due to the complexity of the issues, it is important to find a partner who can cover all the necessary competencies and take them into account in the development process. This is where the EDAG Group can score points with its extensive service portfolio and wealth of experience. Here, customers can be sure that both regulatory and technical issues will be addressed and solutions developed that not only improve the device but also focus on its integration into the medical ecosystem on the user side.
Technical support includes secure cloud-to-chip architecture in accordance with IEC 62304, ISO 14971, MDR Annex I, 17.2, retrofitting of existing devices, gateway design for hospital networks, test & verification packages (IEC 62304 / IEC 60601), and cybersecurity and data protection.
EDAG experts can also offer extensive support at the process level where needed, such as regulatory impact assessments for each update, ISO 13485-compliant QMS integration and process templates, risk management and clinical evaluations in accordance with ISO 14971 and MDR, communication with notified bodies and audit support, as well as pilot rollouts and clinical safeguards.
Customers benefit from validated security and update strategies that are already normatively secured, as EDAG transfers proven OTA concepts from safety-critical industries, such as automotive, to the medtech domain. This combination of engineering expertise and regulatory know-how is cultivated in interdisciplinary teams. They contribute to fast, efficient development processes that are geared towards smooth market approval right from the start.
As a medical device manufacturer, are you also faced with the task of integrating connectivity functions into your portfolio that not only meet regulatory requirements but also fulfill the expectations of users and patients in terms of safety and reliability? Then talk to Sinem Atilgan, Specialist Consultant for Digital Transformation , Tobias Schunk, Project Manager Software & Digitalization , or Michael Kelnberger, Sales Manager Technical Sales at EDAG.
And download our white paper "How to avoid the pitfalls of developing connected medical devices" right here. Here you will find further details on the regulatory requirements and how you can implement them technically, as well as a case study on the OTA retrofit of a digital ECG device. Last but not least, a checklist for an impact analysis is also included as a decision-making aid for the development process.





